
Mercury for EcoStruxure™ Plant Cybersecurity
Protect your OT network and communications with advanced industrial cybersecurity
Published by
Enigmedia

Mercury for EcoStruxure™ Plant Cybersecurity
Published by
Enigmedia
Features
Solution - Connected Products Layer
Sensors, Harmony Hub, Energy Meters
These products include:
• Any connected product acting as end point equipment providing data to the cloud for app and analytics.
• Any connected product acting as intermediate equipment to collect data to the cloud for app and analytics.
Solution - Edge Control Layer
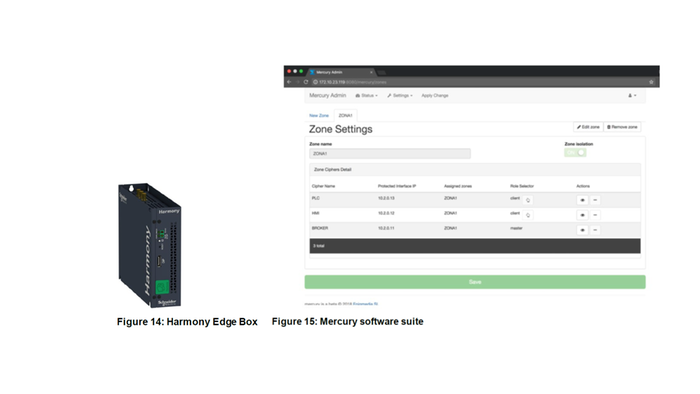
Harmony Edge Box from Schneider Electric
The Harmony Edge Box is employed by this solution as the preferred security enhanced hardware container for embedding the Mercury Cipher from Enigmedia. Thanks to its embedded trusted platform module (TPM), the Harmony Edge Box supports the encryption features needed to manage the secret keys. This is mandatory to provide enhanced security for authentication and encryption, and to help secure communications in the OT plant.
The Harmony Edge Box is plugged in at the top of your current application, so there is no need to stop or modify your control application.
The versatile industrial design capitalizes on multiple hardware and software combinations to address both industrial PC and IIoT wiring needs.
Mercury Cipher from Enigmedia
Mercury is a software-based suite of native ICS cybersecurity products, which is truly hardware-agnostic. Mercury products can be deployed using customer preferred appliances. For full functionality and interoperability, we recommend modern Intel or ARM architectures with Linux-based platforms. If you have a different use case, our engineers can customize our products and adapt them to your specific needs. Deployment of Mercury cybersecurity products is easy and fast. You don't need to change any existing configuration or IP address. Mercury products are transparent to the existing ICS network. Our ICS Encryption is unique and can encrypt and help protect your data and traffic at Layer 2, adding negligible latency to the existing industrial process and with no impact to the communications from PLCs to SCADA. Depending on the use case and the cybersecurity challenge, Mercury is deployed in the OT network in different strategic locations: connected to a mirroring port for enhanced security data collection; deployed to connect remote sites through authenticated and encrypted channels; or deployed inline to create enhanced security zones and define firewalls in conformity with IEC-62443.
![Solution - Edge Control Layer]()
Solution - Apps Analytics & Services Layer
This solution is compatible with Schneider Digital advisors with security enhanced connection from the cloud to the IOT gateway and with AVEVA Insight.
Mercury Orchestrator software
Mercury Orchestrator offers a simple and intuitive panel to configure and manage the Mercury features. It can be deployed on-premise, or cloud.
Mercury is configured, managed, and monitored, from Mercury Orchestrator. Thanks to its centralized console, authorized users can remotely configure temporary ports and firmware settings, send copies of the traffic to SIEM/SOC, or check operational status. Updates can be performed remotely with enhanced security. The preferred location is in the edge layer on-premises, but optionally can be located in the cloud. It can be hosted in any Harmony Edge Box having an embedded TPM.
![Solution - Apps Analytics & Services Layer]()
Plug & Protect
Mercury ciphers are totally transparent to the industrial network. This means that Mercury adds extra security layer without changing current infrastructure or modifying its components.
Deploying Mercury cipher in the field is seamless and can be done in minutes because it does not require changing any existing configuration. Mercury is vendor and protocol agnostic, ie, compatible with legacy devices and virtually any ethernet protocol.
Inventory
Enigmedia Mercury Products Suite includes inventory functionality to map the devices and connections in an industrial OT network. Mercury Inventory analyzes network traffic and maps devices and connections showing:
• Device manufacturer
• IP address
• Packets size
• Communication Ports
Mercury Inventory is an easy to use, fast, and cost-effective tool for discovering network assets that helps system integrators and end-users sketch the network diagram, identify devices, communication protocols and how they are related.
Perimeter protection and segregation
Users can easily define network segments and secure zones from the Mercury Orchestrator control panel.
Also, they can specify which devices will be part of a specific zone, which ones are authorized to communicate with others, and what protocols will be authorized.
Firewall and definition of conduits
Firewall is essential, as it helps prevent attacks from spreading between zones and devices. With Mercury Orchestrator, it is very easy to manage the configuration of authorized ports and traffic.
Ports can be configured as "permanent ports" or "temporary ports". This functionality is very powerful, as having the ports exposed permanently can pose a risk to the integrity of the network and devices.
Helping to prevent vulnerabilities by armoring the network
Mercury encrypts the traffic that goes through its appliances and distributes the information to validated endpoints.
Mercury is designed for ICS/OT environment. Mercury ciphers the industrial protocols adding less than 1 ms latency. Mercury provides extensive vulnerability masking, limiting the available attack surface. The end-point devices simply ignore other unknown or unapproved access attempts.
Most of the advanced attacks in OT need to gather information from the targeted infrastructure as a first step. By cloaking the network, a malicious adversary is not able to perform such actions since the asset cannot be seen.
Mercury architecture encrypts and obfuscates the network while providing visibility to authorized users. This architecture is compatible with DPI/IDS/IPS solutions.
Threat detection and security monitoring
Mercury helps prevent attacks to the network, whether they are connection attempts through unauthorized protocols, network scanning, or denial of service attacks. This prevention capability can be combined with the monitoring of suspicious behavior, through centralized management of logs.
The Mercury Orchestrator server centralizes the logs of each Mercury Cipher which can be integrated with Security Incident Event Management (SIEM) monitoring tools, to detect and manage alerts as well as suspicious behavior.
The solution is compatible with 3rd party products such as IDS/IPS and SIEMs.
Mercury approach helps prevent incidents, reduces complexity and standardize events to simplify correlation processes and help to avoid false-positive alarms.
Mercury OS
Mercury enjoys a hardened Mercury OS specifically designed for industrial network requirements, and considering “availability” as the main value to preserve. To prevent for attacks against firmware manipulation, Mercury Operating System (Mercury OS) uses a combination of security features to protect content store and allowing autostart without human interaction.
Among others, Mercury OS includes:
Secure boot
Full disk encryption
Anti-tampering
Host IDS
OTA (over-the-air) signed firmware updates
Hardware watchdog
Alerts and logs management
Quick and robust remote access
Mercury is a secure, robust and easy to deploy solution that enables remote connection via WiFi/GSM/2G/3G/LTE, compatible with interfaces, devices, and protocols and is directly applicable to any infrastructure without replacing devices or changing configurations.
Mercury is configured, managed, and monitored, from Mercury Orchestrator. Thanks to its centralized console, authorized users can remotely configure temporary ports, FW settings, send copies of the traffic to SIEM/SOC or check operational status. Updates can be done remotely and completely secure.
Mercury Ciphers provides a TPM, Firewall features and enforces authentication and encryption in the channel. Also have several features for preventing DoS attacks and send alerts to the SIEM if detect any suspicious behaviour in the network. Different roles are supported in order to avoid privilege escalation.
![Quick and robust remote access]()
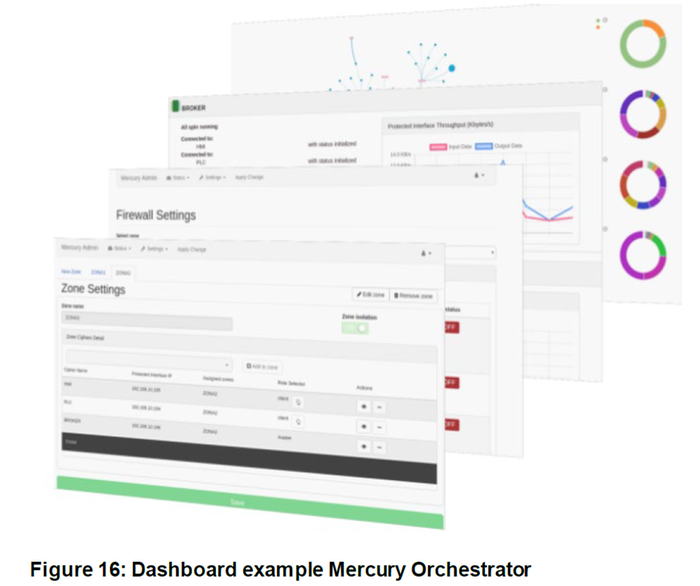
Centralized Management
Mercury Orchestrator offers a simple and intuitive panel to configure and manage all Mercury features and ciphers remotely from a unique dashboard.
These functionalities have been designed to offer the required tools to protect the network in accordance with the best practices and recommendations of IEC-62443 Norm and other organizations.
The dashboard implements different roles such as administrator, engineer and operator with different capabilities.
Note that tunneled devices cannot access to the configuration interface.
![Centralized Management]()
Ensure data integrity in industrial communications
Mercury ciphers implement strong authentication mechanisms such as certificates used to provide mutual authentication. A public key infrastructure (PKI) is managed according to X.509 standard. In addition, symmetric encryption schemes prevent a third party from capturing the communication in an intelligible format.
Further, to ensure that the communication cannot be altered in transit without detection, security mechanisms such as hash-functions and time-stamping are used. These techniques allow us to verify data quality transmitted through the production network.
Mercury ciphers include TPM (Trusted Platform Module) to store private keys and secrets. Thanks to that, hardware appliances can erase secrets and private keys in case of tamper break.
Secure remote access and connections
Mercury is a robust and easy to deploy solution that provides enhanced security by enabling remote connection via WIFI/GSM/2G/3G/LTE. It is compatible with interfaces, devices, and protocols and is directly applicable to any infrastructure without replacing devices or changing configurations.
Mercury is configured, managed, and monitored from Mercury Orchestrator. Thanks to its centralized console, authorized users can remotely configure temporary ports, firmware settings, and send copies of the traffic to SIEM/SOC or check operational status. Updates can be performed remotely in a security enhanced environment.
Mercury Ciphers provide a trusted platform module (TPM), firewall features, and enforces authentication and encryption in the channel. It also provides several features for helping to prevent Denial of Service (DoS) attacks and sends alerts to the SIEM if it detects suspicious network behavior. Different roles are supported in order to avoid privilege escalation.
Thanks to the temporal firewall rules and different role assignments, plant operators can grant access to maintenance providers in a controlled and auditable manner in an enhanced security environment. Tunneled devices cannot access to the configuration interface.
Solution - Connected Products Layer
Sensors, Harmony Hub, Energy Meters
These products include:
• Any connected product acting as end point equipment providing data to the cloud for app and analytics.
• Any connected product acting as intermediate equipment to collect data to the cloud for app and analytics.
Solution - Edge Control Layer
Harmony Edge Box from Schneider Electric
The Harmony Edge Box is employed by this solution as the preferred security enhanced hardware container for embedding the Mercury Cipher from Enigmedia. Thanks to its embedded trusted platform module (TPM), the Harmony Edge Box supports the encryption features needed to manage the secret keys. This is mandatory to provide enhanced security for authentication and encryption, and to help secure communications in the OT plant.
The Harmony Edge Box is plugged in at the top of your current application, so there is no need to stop or modify your control application.
The versatile industrial design capitalizes on multiple hardware and software combinations to address both industrial PC and IIoT wiring needs.
Mercury Cipher from Enigmedia
Mercury is a software-based suite of native ICS cybersecurity products, which is truly hardware-agnostic. Mercury products can be deployed using customer preferred appliances. For full functionality and interoperability, we recommend modern Intel or ARM architectures with Linux-based platforms. If you have a different use case, our engineers can customize our products and adapt them to your specific needs. Deployment of Mercury cybersecurity products is easy and fast. You don't need to change any existing configuration or IP address. Mercury products are transparent to the existing ICS network. Our ICS Encryption is unique and can encrypt and help protect your data and traffic at Layer 2, adding negligible latency to the existing industrial process and with no impact to the communications from PLCs to SCADA. Depending on the use case and the cybersecurity challenge, Mercury is deployed in the OT network in different strategic locations: connected to a mirroring port for enhanced security data collection; deployed to connect remote sites through authenticated and encrypted channels; or deployed inline to create enhanced security zones and define firewalls in conformity with IEC-62443.
Solution - Apps Analytics & Services Layer
This solution is compatible with Schneider Digital advisors with security enhanced connection from the cloud to the IOT gateway and with AVEVA Insight.
Mercury Orchestrator software
Mercury Orchestrator offers a simple and intuitive panel to configure and manage the Mercury features. It can be deployed on-premise, or cloud.
Mercury is configured, managed, and monitored, from Mercury Orchestrator. Thanks to its centralized console, authorized users can remotely configure temporary ports and firmware settings, send copies of the traffic to SIEM/SOC, or check operational status. Updates can be performed remotely with enhanced security. The preferred location is in the edge layer on-premises, but optionally can be located in the cloud. It can be hosted in any Harmony Edge Box having an embedded TPM.
Plug & Protect
Mercury ciphers are totally transparent to the industrial network. This means that Mercury adds extra security layer without changing current infrastructure or modifying its components.
Deploying Mercury cipher in the field is seamless and can be done in minutes because it does not require changing any existing configuration. Mercury is vendor and protocol agnostic, ie, compatible with legacy devices and virtually any ethernet protocol.
Inventory
Enigmedia Mercury Products Suite includes inventory functionality to map the devices and connections in an industrial OT network. Mercury Inventory analyzes network traffic and maps devices and connections showing:
• Device manufacturer
• IP address
• Packets size
• Communication Ports
Mercury Inventory is an easy to use, fast, and cost-effective tool for discovering network assets that helps system integrators and end-users sketch the network diagram, identify devices, communication protocols and how they are related.
Perimeter protection and segregation
Users can easily define network segments and secure zones from the Mercury Orchestrator control panel.
Also, they can specify which devices will be part of a specific zone, which ones are authorized to communicate with others, and what protocols will be authorized.
Firewall and definition of conduits
Firewall is essential, as it helps prevent attacks from spreading between zones and devices. With Mercury Orchestrator, it is very easy to manage the configuration of authorized ports and traffic.
Ports can be configured as "permanent ports" or "temporary ports". This functionality is very powerful, as having the ports exposed permanently can pose a risk to the integrity of the network and devices.
Helping to prevent vulnerabilities by armoring the network
Mercury encrypts the traffic that goes through its appliances and distributes the information to validated endpoints.
Mercury is designed for ICS/OT environment. Mercury ciphers the industrial protocols adding less than 1 ms latency. Mercury provides extensive vulnerability masking, limiting the available attack surface. The end-point devices simply ignore other unknown or unapproved access attempts.
Most of the advanced attacks in OT need to gather information from the targeted infrastructure as a first step. By cloaking the network, a malicious adversary is not able to perform such actions since the asset cannot be seen.
Mercury architecture encrypts and obfuscates the network while providing visibility to authorized users. This architecture is compatible with DPI/IDS/IPS solutions.
Threat detection and security monitoring
Mercury helps prevent attacks to the network, whether they are connection attempts through unauthorized protocols, network scanning, or denial of service attacks. This prevention capability can be combined with the monitoring of suspicious behavior, through centralized management of logs.
The Mercury Orchestrator server centralizes the logs of each Mercury Cipher which can be integrated with Security Incident Event Management (SIEM) monitoring tools, to detect and manage alerts as well as suspicious behavior.
The solution is compatible with 3rd party products such as IDS/IPS and SIEMs.
Mercury approach helps prevent incidents, reduces complexity and standardize events to simplify correlation processes and help to avoid false-positive alarms.
Mercury OS
Mercury enjoys a hardened Mercury OS specifically designed for industrial network requirements, and considering “availability” as the main value to preserve. To prevent for attacks against firmware manipulation, Mercury Operating System (Mercury OS) uses a combination of security features to protect content store and allowing autostart without human interaction.
Among others, Mercury OS includes:
Secure boot
Full disk encryption
Anti-tampering
Host IDS
OTA (over-the-air) signed firmware updates
Hardware watchdog
Alerts and logs management
Quick and robust remote access
Mercury is a secure, robust and easy to deploy solution that enables remote connection via WiFi/GSM/2G/3G/LTE, compatible with interfaces, devices, and protocols and is directly applicable to any infrastructure without replacing devices or changing configurations.
Mercury is configured, managed, and monitored, from Mercury Orchestrator. Thanks to its centralized console, authorized users can remotely configure temporary ports, FW settings, send copies of the traffic to SIEM/SOC or check operational status. Updates can be done remotely and completely secure.
Mercury Ciphers provides a TPM, Firewall features and enforces authentication and encryption in the channel. Also have several features for preventing DoS attacks and send alerts to the SIEM if detect any suspicious behaviour in the network. Different roles are supported in order to avoid privilege escalation.

Centralized Management
Mercury Orchestrator offers a simple and intuitive panel to configure and manage all Mercury features and ciphers remotely from a unique dashboard.
These functionalities have been designed to offer the required tools to protect the network in accordance with the best practices and recommendations of IEC-62443 Norm and other organizations.
The dashboard implements different roles such as administrator, engineer and operator with different capabilities.
Note that tunneled devices cannot access to the configuration interface.

Ensure data integrity in industrial communications
Mercury ciphers implement strong authentication mechanisms such as certificates used to provide mutual authentication. A public key infrastructure (PKI) is managed according to X.509 standard. In addition, symmetric encryption schemes prevent a third party from capturing the communication in an intelligible format.
Further, to ensure that the communication cannot be altered in transit without detection, security mechanisms such as hash-functions and time-stamping are used. These techniques allow us to verify data quality transmitted through the production network.
Mercury ciphers include TPM (Trusted Platform Module) to store private keys and secrets. Thanks to that, hardware appliances can erase secrets and private keys in case of tamper break.
Secure remote access and connections
Mercury is a robust and easy to deploy solution that provides enhanced security by enabling remote connection via WIFI/GSM/2G/3G/LTE. It is compatible with interfaces, devices, and protocols and is directly applicable to any infrastructure without replacing devices or changing configurations.
Mercury is configured, managed, and monitored from Mercury Orchestrator. Thanks to its centralized console, authorized users can remotely configure temporary ports, firmware settings, and send copies of the traffic to SIEM/SOC or check operational status. Updates can be performed remotely in a security enhanced environment.
Mercury Ciphers provide a trusted platform module (TPM), firewall features, and enforces authentication and encryption in the channel. It also provides several features for helping to prevent Denial of Service (DoS) attacks and sends alerts to the SIEM if it detects suspicious network behavior. Different roles are supported in order to avoid privilege escalation.
Thanks to the temporal firewall rules and different role assignments, plant operators can grant access to maintenance providers in a controlled and auditable manner in an enhanced security environment. Tunneled devices cannot access to the configuration interface.